
Background
In the world of user-controlled digital credentials, one thing has become clear – it’s not a question of if these technologies will be adopted, but when. Decision-makers from both public and private sectors around the world are increasingly inclined to integrate digital credentials into their organisations and ecosystems.
Once the choice to adopt user-controlled digital credentials is set, a fresh challenge pops up: navigating the sea of standards and tech options out there. Diving into the technical details of specifications can be overwhelming, especially when trying to weigh business requirements and other contextual factors against the many options available. The mountain of documentation doesn’t help either. It’s all too easy to get swamped by the choices and feel lost. Plus, grasping the subtle differences and trade-offs between specifications can be quite the hurdle.
So, is there a solution to simplify the process of selecting credential exchange protocols? Can we make it easier for individuals to choose the right option based on their specific context and requirements?
The Credential Exchange Protocols Task Force
At the Internet Identity Workshop, IIW 36, held in April 2023, we called a session titled “Creating a Credential Exchange Protocols Comparison Matrix”.
The concept arose from the need to address a prevalent issue and the desire to develop something akin to the credential profile comparison matrix, created by various contributors over the past year or so. The goal was to explore the possibility of achieving similar outcomes with credential exchange protocols. The session garnered significant interest, indicating a genuine commitment to advancing this effort.
To ensure a solid foundation for this initiative, we decided to find a home for it. The Trust over IP (ToIP) Foundation emerged as the ideal host, thanks to its community of experts, its welcoming and open culture, and its alignment with our goals. This effort primarily aims to enrich documentation around ToIP Layer 3 Trust Tasks related to credential exchange, which are among the most discussed trust tasks today. For the vision of digital trust within the ToIP architecture to be realised, we need to streamline the process for those building trust applications that rely on digital credential exchanges.
Consequently, a dedicated Task Force within the Technology Stack Working Group was founded: The Credential Exchange Protocols Task Force. This group convenes weekly with a shared goal of driving this crucial work forward.
What has the Task Force accomplished to-date?
- Since forming the task force, we have created a first version of the comparison criteria for digital credential issuance and presentation protocols:
| Categories | Sub-categories |
| 1. Protocol Objective(s) | A. Protocol Objective(s) |
| 2. Protocol Governance | A. Specification Link and Versioning B. Specification Status/Maturity C. Specification Body D. Open Source / Intellectual Property Rights |
| 3. Features | A. Architecture Model B. Support for Additional Trust Tasks C. Communications Context D. Security E. Privacy F. Performance/Scalability Constraints G. Initiation Mechanism(s) H. Transport Mechanism(s) I. Authentication J. Identifiers Types Supported K. Credential Formats Supports L. Compliance to Data Privacy Laws M. Static Endpoint Discovery Process N. Dynamic Endpoint Support O. Additional Features |
| 4. Use Cases | A. Use Case Flexibility B. Offline/Online Support C. Designed for Mobile Device Use D. Designed for Web Browser Use E. Support for Cross-device Flows F. Rigidity and Flexibility of Protocol |
| 5. Adoption | A. Technology Readiness Level (TRL) B. Deployment Viability C. Current Implementations D. Education Requirements E. Deployment Complexity F. Implementation Standards |
- The group has fully documented these four issuance protocols against the above comparison criteria:
- ACDC
- ISO 23220-3
- Issue Credential v2
- OpenID4VCI
Here’s a sneak peek at what the comparison matrix is looking like:
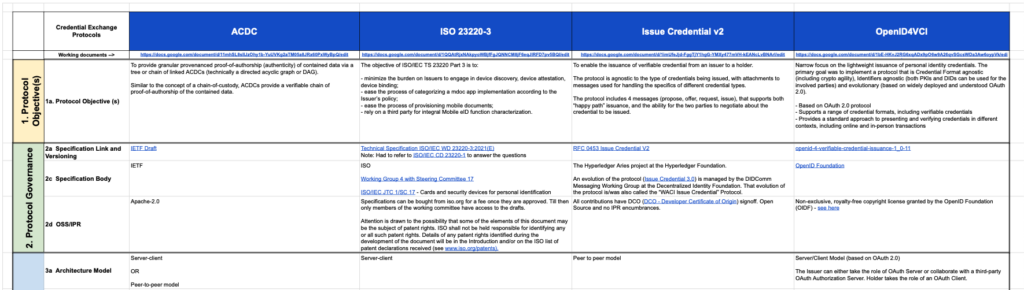
The first version of the documentation is available here: https://docs.google.com/spreadsheets/d/1_KKQZmmNRnEME96fZCPbMW-TC9j0tQ-dVuk5zzKa8U8/edit#gid=1229620925.
Note that for the first version of the comparison matrix, we wanted to select a small number of protocols based on where the working group is seeing market demand. Since this effort is a lot of work, we also wanted to start small so that we could achieve a realistic version 1.
IIW 37
Because this effort was started by a session at the last Internet Identity Workshop (IIW), it made sense that we reconvene at IIW 37, this in October 10-12 at the Computer Science Museum in Mountain View, California.
During this event, we will call a session to provide an overview of the progress achieved so far. We will seek feedback from the community and implementers of digital credentialing infrastructure. This input is invaluable as it guides our task force toward the most beneficial direction for all stakeholders.
What are we working on next?
- We will continue to refine the issuance protocols matrix. Our vision is to create a lightweight ‘cheat-sheet’ type of document, that will refer to further documentation underneath for anyone wishing to go deeper.
- We will start working on documenting the presentation protocols against the same common set of criteria.
- We want to start involving any architect or technical product owners that are decision makers or make recommendations on digital credential strategy, so that we can ensure that we’re creating a valuable document for them.
Want to get involved?
Our Task Force holds meetings every Wednesday at NA/EU: 09:00-10:00 ET / 15:00-16:00 CET. You can find the calendar event here. Please feel free to join our next meeting on October 18, 2023.

