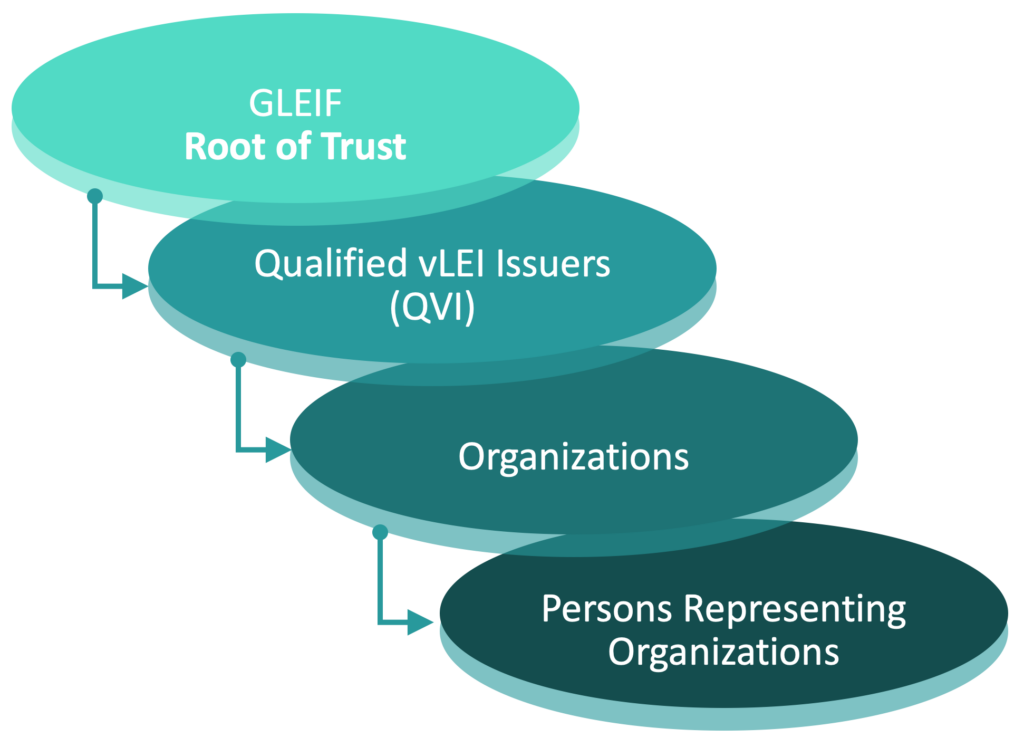
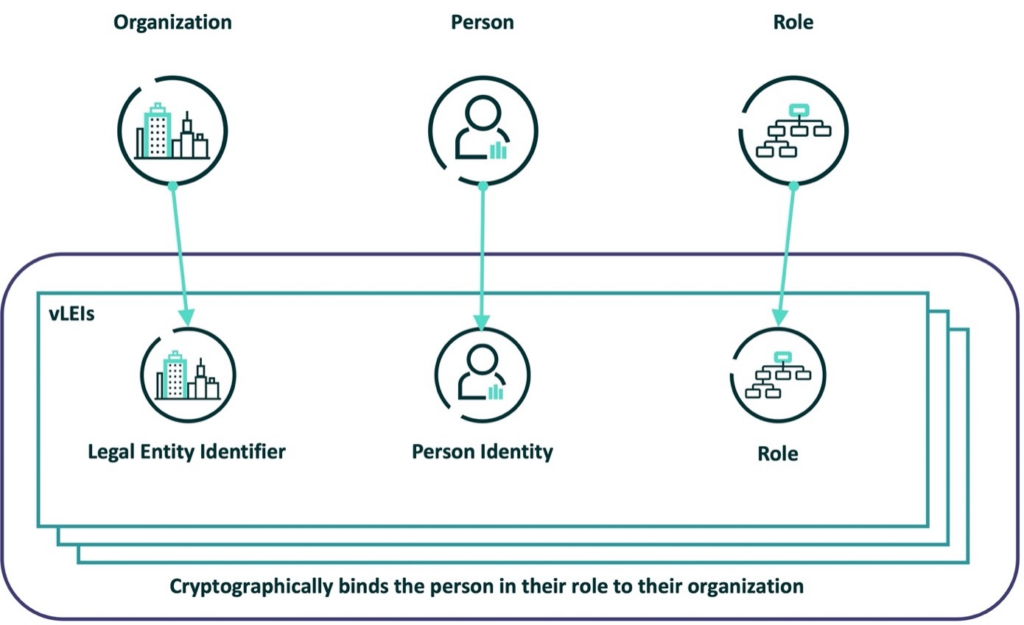
By Eric Drury
If you’re in the digital trust space, like me you might be encouraged by the number and variety of inspiring developments—appearing on an almost weekly basis—which illustrate the momentum that responsible technology is gaining in the drive towards a more trustworthy and sustainable future.
One of the latest and more interesting initiatives comes—yet again—from the Kingdom of Bhutan in the form of Gelephu Mindfulness City (GMC). GMC is the Kingdom’s unique version of a smart city. They call it a Special Administrative Region, integrating economic growth with mindfulness, holistic living, and sustainability.
How does digital trust fit into GMC?
In October of last year, Bhutan launched the world’s first self-sovereign national digital identity system, Bhutan NDI. And as a pillar of digital public infrastructure (DPI), a digital identity system forms the basis for trusted interactions between individuals, government, and business.
The NDI system, which Bhutan is currently rolling out nation-wide, will be part of the core infrastructure that provides cutting-edge digital connectivity for GMC. As such, this is an exciting opportunity to further cement the viability of emerging SSI and other trust technologies for implementation at population scale.
Trust Over IP is proud to have contributed to Bhutan’s NDI system both formally and informally.
Drummond Reed, one of ToIP’s founding board members, provided inspiration—and a road map of sorts—for the development of SSI systems via the book he co-authored called ‘Self-Sovereign Identity – Decentralized Digital Identity and Verifiable Credentials’. Drummond and other ToIP members also provided expertise and input for Bhutan’s National Digital Identity Act, the NDI Act of Bhutan, relying heavily on the ToIP governance metamodel which was developed by the ToIP’s Governance Stack Working Group led by Scott Perry.
For an in-depth case study on the Bhutan NDI program, refer to Bhutan NDI, Digital Trust Ecosystem, written by DHI’s Pallavi Sharma and Eric Drury, co-chair of ToIP’s Ecosystem Foundry Working Group.
Trust Over IP and Gelephu Mindfulness City further align in that both espouse the intertwining of governance and technology as a core enabler of digital trust.
- From a governance perspective, GMC blends robust policies that ‘build trust and accountability with mindful incentives designed to empower both residents and businesses alike to reach their fullest potential’.
- From a technology perspective, Gelephu Mindfulness City will be built on a foundation of ‘world-class infrastructure seamlessly integrating state-of-the-art technology with sustainable practices’.
In support of GMC, the Kingdom is convening the first Bhutan Innovation Forum (BIF), a global initiative uniting international leaders, innovators, and entrepreneurs to support Bhutan’s vision of a Mindfulness City.
The BIF takes place in less than two weeks, October 1-3, 2024. ToIP members Drummond Reed and Eric Drury are honored to be invited to attend, representing the ToIP community and continuing the engagement with Bhutan’s digital trust community.
Drummond and Eric will appear on panels to promote the principles of digital trust and will share their experience and expertise on all things digital trust, including the emergence of cross-border digital trust networks.
ToIP is thrilled to once again walk the path with Bhutan towards a more sustainable, trustworthy, and equitable digital future. We look forward to sharing our learnings after the Forum so that the entire digital trust community benefits.